
Zero Trust is a gold standard of business security that is rapidly becoming a standard principle, and it’s not difficult to understand why. With the shift to hybrid work and cloud-based collaboration, legacy security models are reworked as a vulnerability area. Microsoft 365 brings with it a vast attack surface with openness and active user engagement.
But what, in practical terms, does Zero Trust mean for the way things are managed? And how is it possible to implement these concepts into a platform as dense and complex as Microsoft 365?
This paper is a brief, step-by-step tutorial on understanding what Zero Trust is when implemented in Microsoft 365, and how its principles can be applied efficiently with an up-to-date, user-centric governance model.
1- What is the Zero Trust Model?
At its core, Zero Trust is a security model founded upon a healthy attitude: “Never trust, always verify.”
Let’s break down the three foundations of this model:
- Explicit Verification
Every user, device, and app will have to prove who they are under stringent terms. That encompasses Multi-Factor Authentication (MFA), biometrics, and behaviour-based identity assurance.
- Least Privilege Access
Access is not defaulted. It is granted adequately and only for the duration needed. That holds for files, Teams, mailboxes; all of it.
- Assume Breach
Zero Trust assumes the attacker is already inside. So your system must be architected with constant watching and damage control in mind.
2- Why Zero Trust Matters More Than Ever in Microsoft 365?
Microsoft 365 is the backbone of modern work. But it’s also one of the most exposed digital environments.
- Frequent internal and external sharing
- A growing number of teams, channels, groups, sites, and mailboxes
- Accumulation of access rights over time
- Few built-in mechanisms to identify excessive privileges or inactive accounts
3- What Are the Zero Trust Principles of Microsoft 365?
Here’s how Microsoft frames Zero Trust within its ecosystem:
- Strong Identity Verification
Use Azure AD Conditional Access to enforce identity requirements and block risky logins. MFA is not optional, it’s essential.
- Role-Based Access and Segmentation
Every user should be assigned just the right permissions for their job. Nothing more. Implementing role-based access control (RBAC) ensures containment if one account is compromised.
- Real-Time Monitoring
Leveraging Microsoft Defender for Cloud Apps, logs, and behavioural analytics helps detect unusual patterns, like sudden downloads or sign-ins from new locations.
- Automated Response
Zero Trust isn’t just about seeing the risk, it’s about automating your response to it. Policy-based automation is key.
- Protecting Data at the Core
Classify and label sensitive data. Control access to documents. Leverage Microsoft Information Protection to embed governance into your files themselves.
4- Native Microsoft 365 Tools for Zero Trust
Microsoft does offer tools aligned with Zero Trust, including:
- Secure Score for risk assessment
- Privileged Identity Management (PIM) to control admin access
- Azure AD Conditional Access policies
- Defender for Office 365 for threat detection
But here’s the Catch: These tools are fragmented and often require advanced configuration. They’re powerful but not always accessible to small or mid-sized IT teams.
5- TeamsFox: Applying Zero Trust Without Complexity
TeamsFox was designed with one goal: make Zero Trust governance understandable and actionable. No scripting. No jargon. No piecing together five admin portals.
Built for Everyone: Whether you’re an IT admin or a compliance officer, TeamsFox’s visual dashboards and alerts make governance clear and actionable.
5-1- Smart Sign-in Monitoring
- Sign-ins from unusual geographical locations: Detecting suspicious behaviour
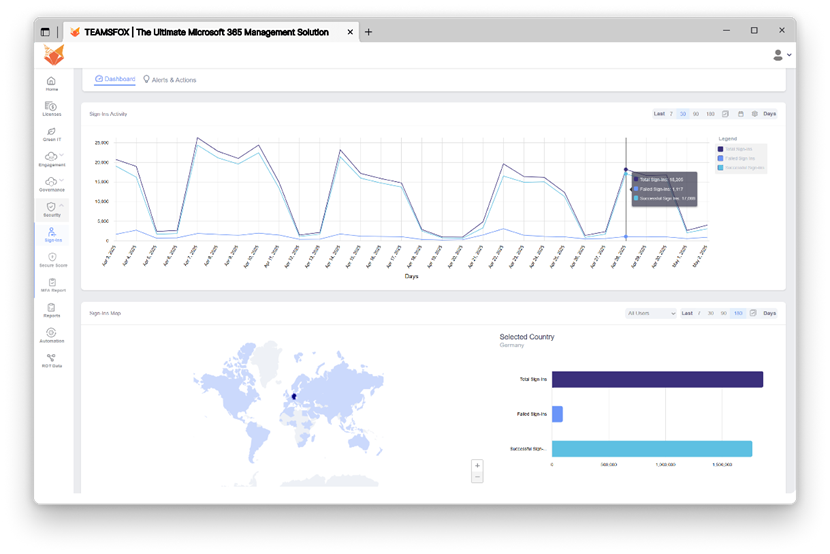
Examples:
Sign-in from a Risky or Unexpected Country
An employee who typically works in France abruptly joins from a nation where your company does not operate, like Russia or North Korea.
This might indicate that threat actors are stealing or abusing credentials.
Multiple Location Jumps in Short Timeframes
Within an hour, a user logs in from London, Dubai, and New York.
These abrupt changes could indicate that multiple attackers are testing the account, which is unrealistic for authorized access.
- Failed sign-ins: Identifying abnormal or unauthorized access attempts
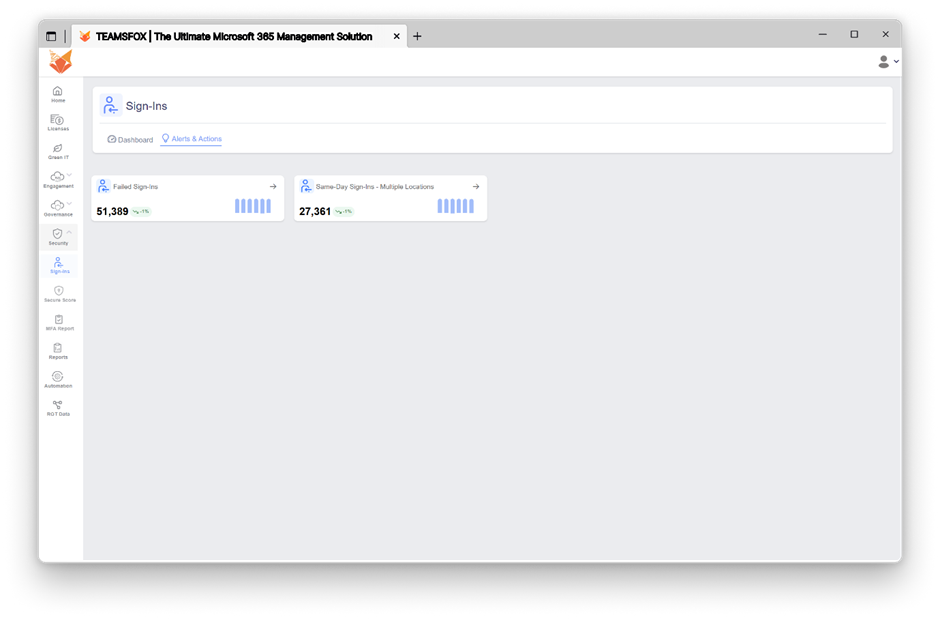
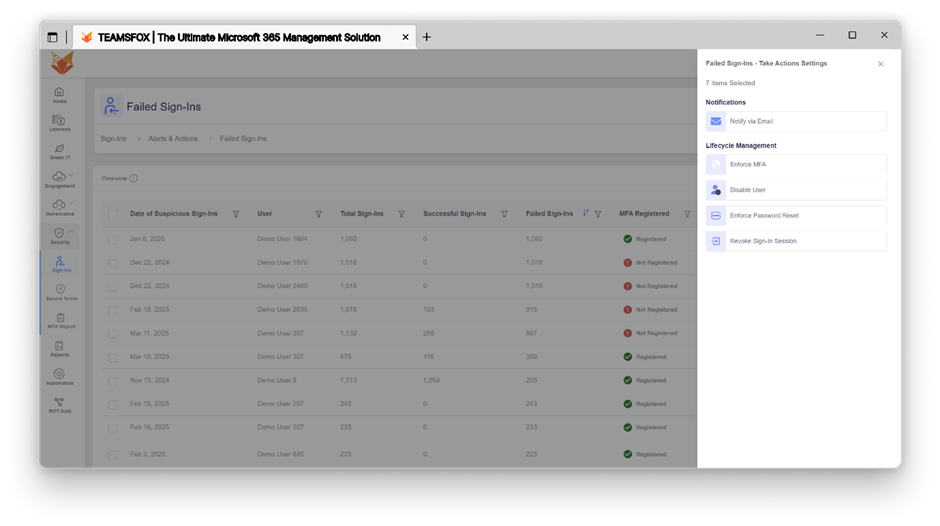
Examples:
Multiple Failed Password Attempts
A brute force attack, in which an attacker attempts to guess the password by trial and error, is suggested when a user account displays dozens of unsuccessful password attempts in a brief amount of time.
Failed MFA Challenge
A legitimate username and password are entered correctly, but the MFA challenge fails repeatedly. This could mean an attacker has stolen the password but cannot bypass the second factor, a clear sign of credential theft.
– MFA Report: Overview of Multi-Factor Authentication status for all users
– Alerts for users without MFA enabled or with misconfigured MFA
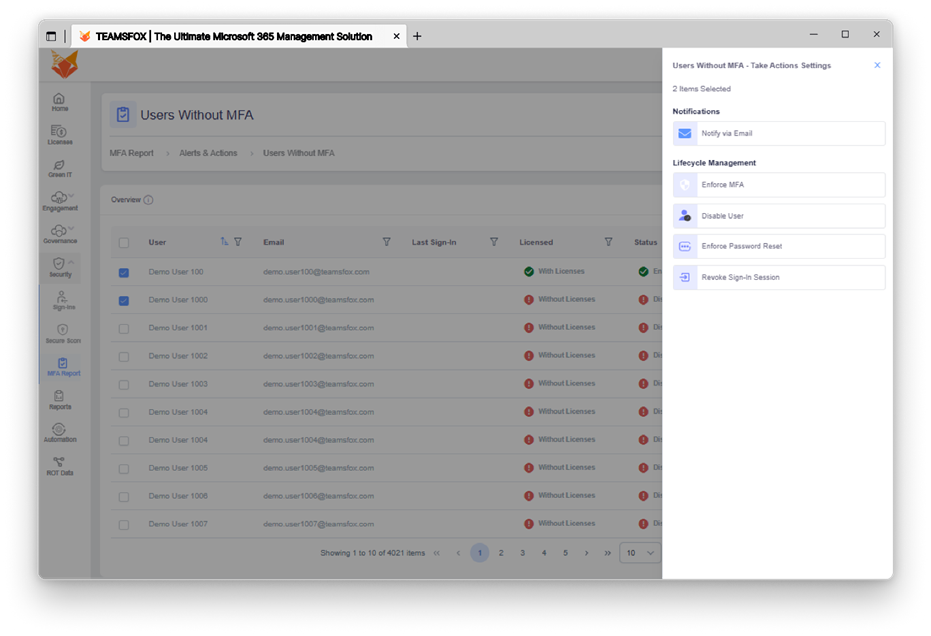
5-2- Granular governance alerts by service
Based on Zero Trust best practices, TeamsFox provides a sophisticated alert system that is divided into the following service categories:
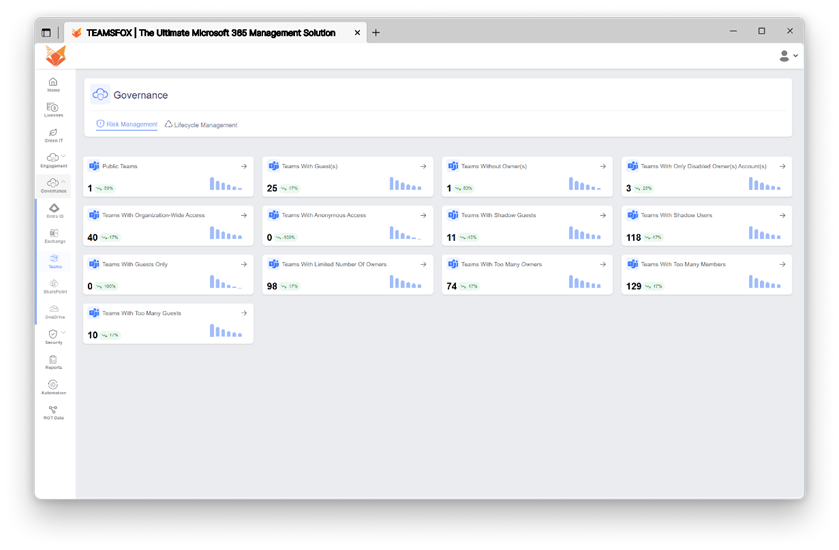
Teams:
- Teams with Organization-Wide Access
Why it matters:
If sensitive files are kept there, this wide access level may easily result in unintentional data exposure. Since Zero Trust requires the least amount of privilege, open access needs to be recognized and, if not required, restricted.
- Anonymous Access or Shadow Guests/Users
Why it matters:
The likelihood of data leaks, phishing, or misuse is significantly increased by external or anonymous access. These need to be identified and audited because Zero Trust necessitates controlled guest access and explicit verification.
- Teams with Too Many or Too Few Owners, Members, or Guests
Why it matters:
Least privilege is supported by appropriate role assignment. TeamsFox highlights these circumstances so administrators can properly balance membership and ownership.
- Inactive or Archived Teams
Why it matters:
One common blind spot is dormant teams. Sensitive information may be revealed if outdated content remains available. It is advised by Zero Trust to eliminate or limit access to outdated resources.
- Teams with Large Files or Storage Anomalies
Why it matters:
Large files may indicate possible data exfiltration, unintentional data dumps, or illegal uploads. One useful aspect of upholding security hygiene is monitoring these, which aids in enforcing governance and storage policies.
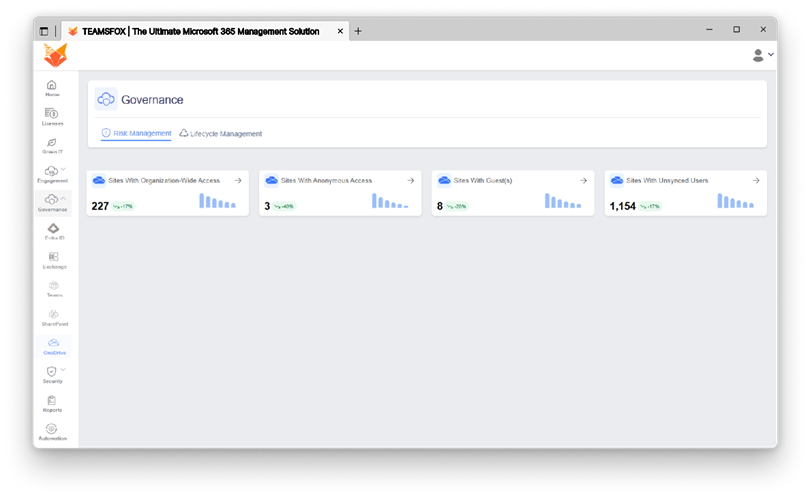
OneDrive:
- Sites with Anonymous or Guest Access
Why it matters:
Of all the reasons accidental data leaks can take place, this incorporates one of the most commonly used. Users can easily share files without realizing their susceptibility to this danger.
The websites hosting these files MUST BE discovered, reviewed, and protected because Zero Trust requires the utmost control on outside sharing and explicit verification.
- Storage Constraints & Large Files
Why it matters:
Large files can reflect suspicious data exfiltration, mass uploads, or backups being conducted without notice. Monitoring storage limits is a key element of Zero Trust’s concept of continual monitoring, and it also helps to enforce policy decisions, to avoid a service interruption, and to alert to an anomalous event before it happens.
- Unsynced Users
Why it matters:
This could indicate that the account is inactive but still contains sensitive data, which could be a blind spot, or that the files are out of date. Zero Trust dictates that you should look into and clean unused or inactive accounts so your attack surfaces are less likely to be attacked.
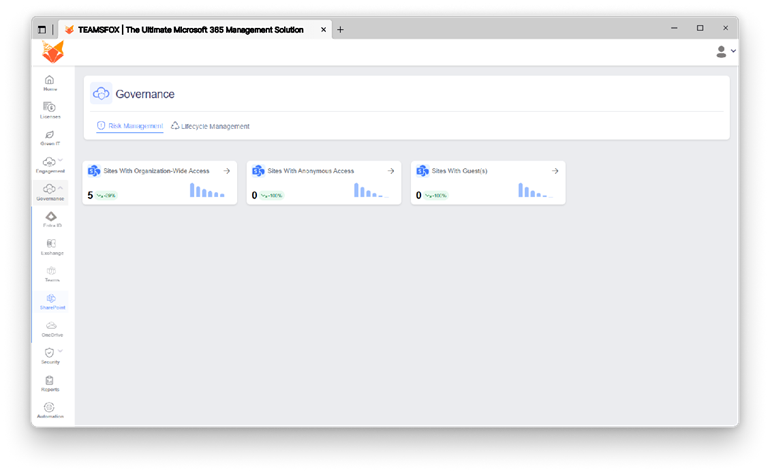
SharePoint:
- Organization-Wide Access
Why it matters:
While it can provide benefits to company-wide resources, sensitive documents are often inadvertently overexposed. Sometimes, the staff will retain confidential documents in locations that they should not even have access to.
Organization-wide websites must be routinely checked for inadvertent disclosures, as Zero Trust requires access to be explicit, and limited to those who need it.
- Anonymous or Guest Access
Why it matters:
External sharing is one of the biggest risk areas in Microsoft 365. If left unchecked, it can lead to data leaks, non-compliance, or unintentional exposure to the public Internet.
Sites with external or anonymous access should be detected and locked down, as Zero Trust principles require that all access is validated, justified, and routinely validated.
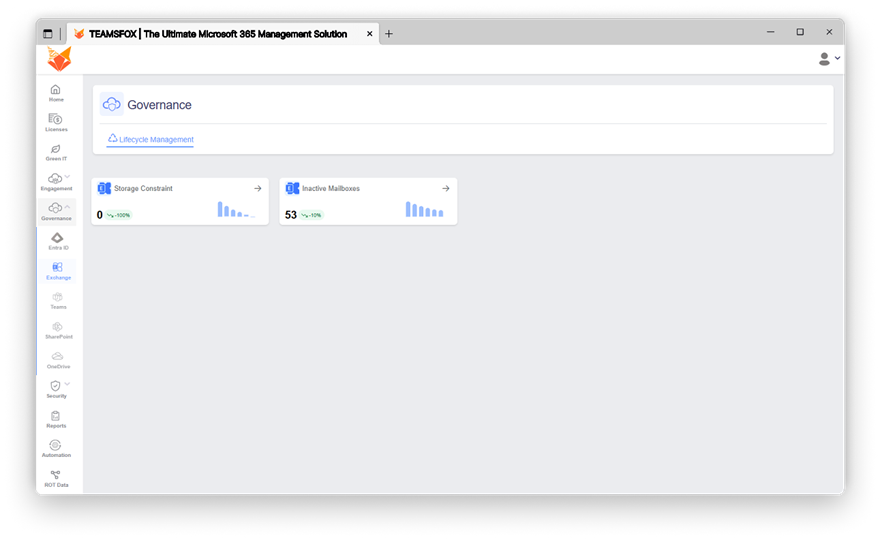
Exchange:
- Inactive Mailboxes
Why it matters:
Sensitive emails and attachments often remain present in inactive mailboxes, and could still contain legitimate credentials or assigned access.
It is wise to identify and remove these mailboxes before they could be exploited by attackers, as Zero Trust requires organizations to acknowledge breaches and retreat as much attack surface area as possible.
- Mailboxes with Storage Constraint
Why it matters:
Users may store emails in personal drives, or other non-secure channels, to save mail space which can expose organizations to data leaks and shadow IT, and similarly, unlimited or near-full mailboxes can create operational risk (missed emails, delivery failures). Given that Zero Trust is so focused on continuous supervision and policy enforcement, discovering and correcting these limitations is a part of communication compliance and security.
EntraID:
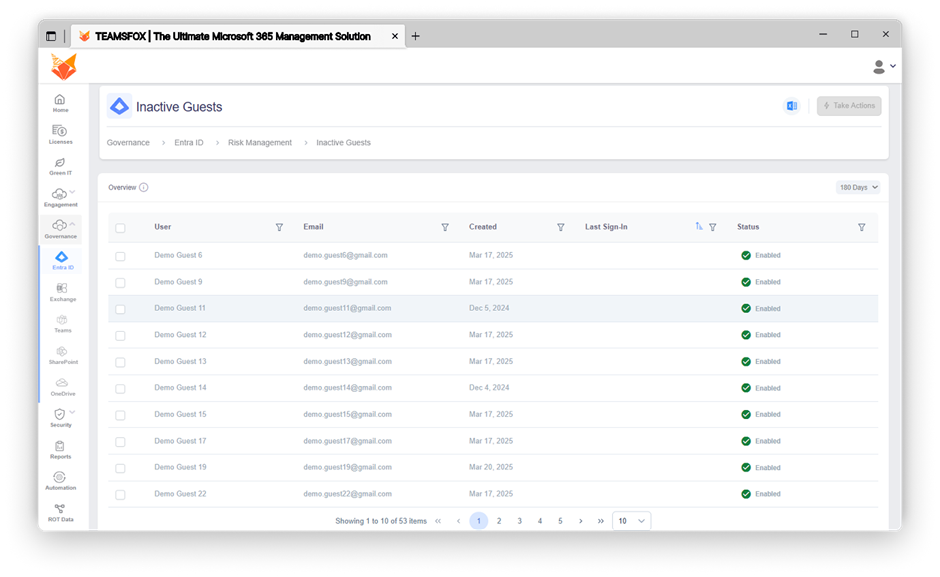
- Inactive Guests
Why it matters:
One security risk that may not be widely recognized is inactive accounts for guest accounts. Inactive guest accounts often retain excessive access long after they are no longer needed, resulting in hackers having a few easy access points to use in the event of stolen credentials or accidentally reused ones.
Because Zero Trust is all about establishing access that is explicit, justified, and regularly reviewed, it is important to identify and delete inactive guests not just for your directory security, but to limit your attack surfaces.
5-3- Automation: From Detection to Action
- Identifying risks is not enough, reacting quickly is key to Zero Trust.
Finding risks is one half of the equation; the other half is reacting quickly. It is essential to achieving Zero Trust.
TeamsFox offers built-in automated capabilities alongside alerting capabilities. This means that organizations can take the corrective action directly from the platform:
Example automated template actions:
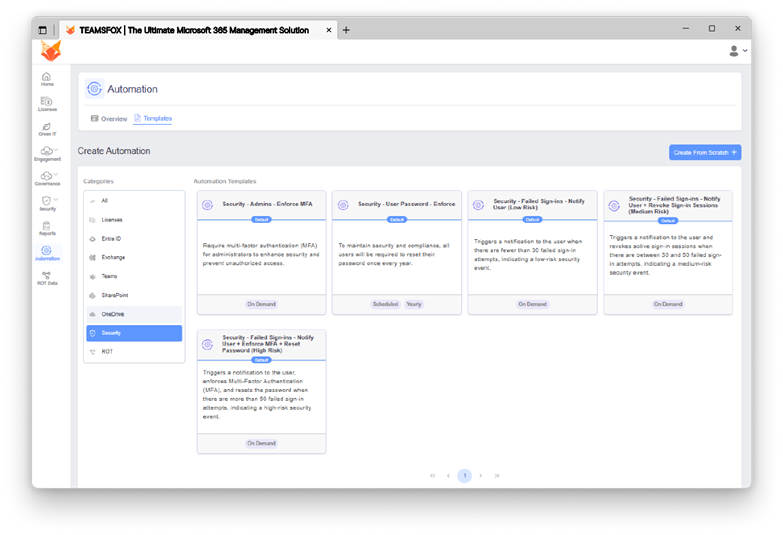
Automation ensures that governance is continuous, scalable, and aligned with your organization’s policies, without requiring manual intervention.
6- Comparison: Microsoft 365 (native) vs TeamsFox
| Feature | Microsoft 365 (native) | TeamsFox |
| Unified access view | ❌ Fragmented | ✅ Consolidated by service |
| Suspicious sign-ins (failure/location) | ⚠️ Technical logs | ✅ Visual and filterable alerts |
| Secure Score | ✅ Yes | ✅ Integrated tracking + risk correlations |
| MFA Report | ⚠️ Complex to centralize | ✅ Clear view + missing MFA alerts |
| Detection of shadow guests/users | ❌ No | ✅ Yes |
| Governance analysis for Teams/SharePoint/etc | ⚠️ Manual scripts | ✅ Automated multi-level alerts |
| Visibility on storage & large files | ❌ Manual | ✅ Alerts on storage anomalies |
Conclusion
In a realm like Microsoft 365, the Zero Trust model is crucial. However, those organizations adopting the model will require suitable tools that can leverage best practices into meaningful, intelligible, and maintainable actions.
We provide a layer of intelligent governance through TeamsFox that enhances and simplifies the Microsoft ecosystem.
Would you like to assess the compliance of your environment with Zero Trust?
Contact us for an audit or begin your free TeamsFox trial.
Comments are closed